M. JAHIN
Projects
ICS/OT Cybersecurity
ICS/OT Cybersecurity
ICS/OT Cybersecurity
Aqua Sentinel - ICS Cybersecurity Capstone Technical Report
ICS/OT Cybersecurity
CEH Penetration Test Report - MD Muhtashim Jahin
Security Operations/Blue Team Projects
Advanced Cybersecurity SOC Lab – Threat Detection, Monitoring, Incident Response & Vulnerability Management
IDS/IPS Setup: SURICATA
An IDS can be implemented as software on a device, dedicated hardware, or a cloud-based solution. An IDS operates in passive mode.
Network Security Engineering & Network Engineering
Information Technology
IT Infrastructure Deployment, System Administration & Monitoring
Network Architecture Project.
Blue Sky Mining Corporation: Remote Site Coalmine Network Architecture
Network Security Engineering
Enterpirse Corporate Network Security Architecture and Configuration for Property Management Firm
Penetration Test/Red Team
Web Application Penetration Testing Report (DVWA)
CEH Penetration Test Report - Md Muhtashim Jahin
ICS/OT Cybersecurity
ICS/OT Cybersecurity
ICS/OT Cybersecurity
INCS-Culminating
ICS/OT Cybersecurity
CEH Penetration Test Report - MD Muhtashim Jahin
Network Security & Engineering
Information Technology
IT Infrastructure Deployment, System Administration & Monitoring
IT & OT Converged Network Architecture Project.
Blue Sky Mining Corporation: Remote Site Coalmine Network Architecture
Network Security Engineering & Configuration
Enterpirse Corporate Network Security Architecture and Configuration for Property Management Firm
Security Operations/Blue Team Projects
Advanced Cybersecurity SOC Lab – Threat Detection, Monitoring, Incident Response & Vulnerability Management
SURICATA
An IDS can be implemented as software on a device, dedicated hardware, or a cloud-based solution. An IDS operates in passive mode.
ICS/OT Cybersecurity
INCS-Culminating
CEH Penetration Test Report - MD Muhtashim Jahin
Security Operations/Blue Team Projects
Advanced Cybersecurity SOC Lab – Threat Detection, Monitoring, Incident Response & Vulnerability Management
SURICATA
An IDS can be implemented as software on a device, dedicated hardware, or a cloud-based solution. An IDS operates in passive mode.
Network Security Engineering & Network Engineering
Information Technology
IT Infrastructure Deployment, System Administration & Monitoring
Network Architecture Project.
Blue Sky Mining Corporation (Remote Site Coalmine Network Architecture)
Network Security Engineering
Enterpirse Corporate Network Security Architecture and Configuration for Property Management Firm
Penetration Test/Red Team
Web Application Penetration Testing Report (DVWA)
CEH Penetration Test Report - Md Muhtashim Jahin
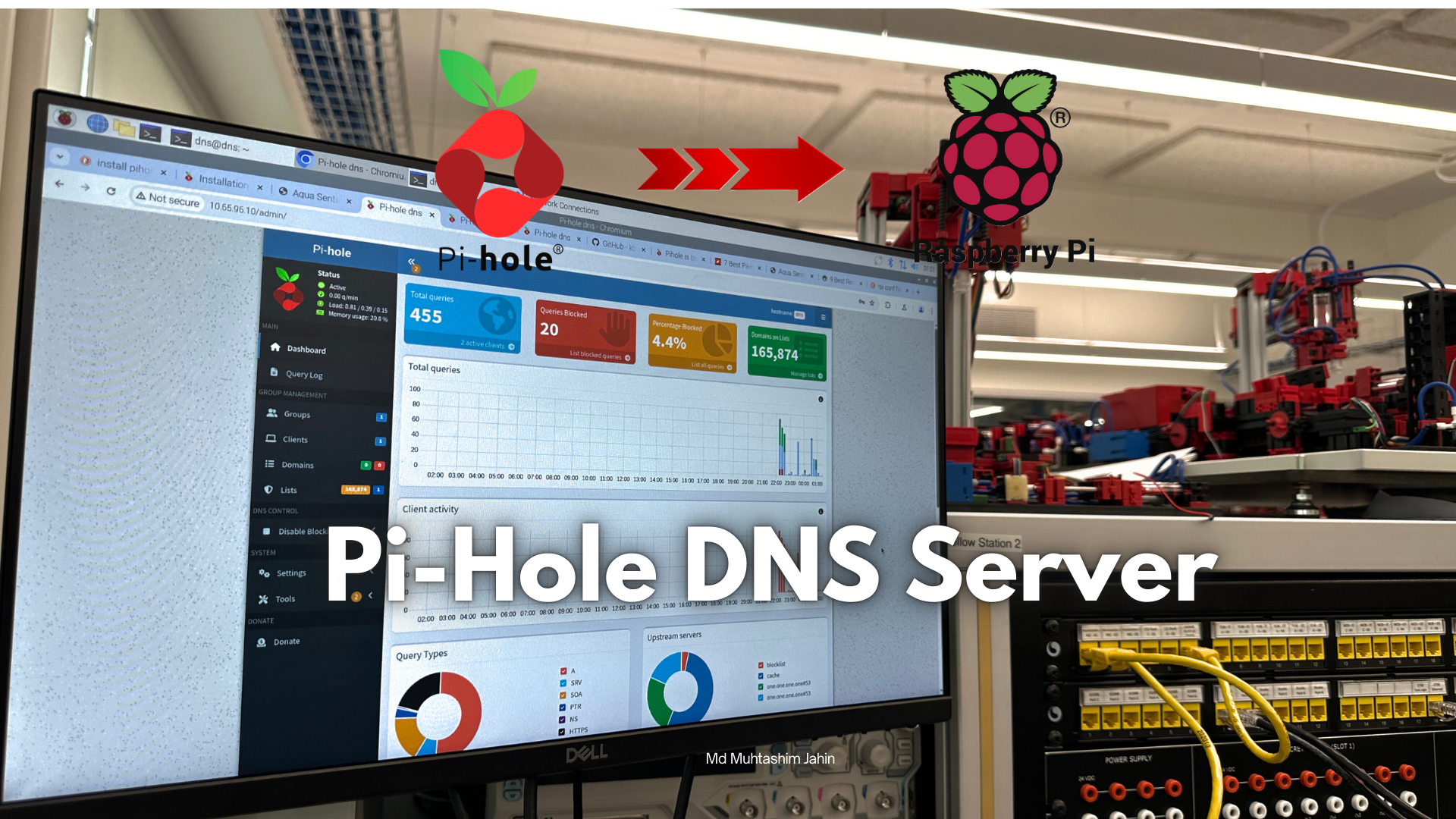
Pi-hole DNS Server on Raspberry Pi 5

Information Technology (IT)

Cybersecurity & Network Security
Internet of Things (IOT)

Operational Technology (OT)